Most security programs are built around assessments that operate by scope. Pentests, compliance audits, and tool-driven reviews all share this constraint. They evaluate environments based on what is allowed, not based on how real attackers behave.
Adversaries do not work inside scopes. They test environments the way engineers test systems. They explore, chain, pivot, escalate, and adapt until they find a viable path to impact. That difference defines the gap between a well-managed audit program and a resilient organization.
This article explains how adversaries actually test enterprise environments and why CISOs increasingly rely on adversary simulation to understand their real exposure.
Pentests Validate Scope. Attackers Validate Opportunity.
Pentesting is a structured exercise designed to identify vulnerabilities within a defined set of boundaries. It is valuable for hygiene, compliance, and verifying known controls.
But it follows rules.
Real attackers do not.
|
How Pentests Operate |
How Adversaries Operate |
|
Predefined scope and rules |
Target identities, not just systems |
|
Limited target sets |
Chain OSINT, cloud misconfigurations, and overlooked permissions |
|
Focused on surface vulnerabilities |
Move across boundaries that tests do not cover |
|
Designed for compliance or basic validation |
Persist quietly while expanding access |
|
Point-in-time view |
Escalate toward business impact |
This is not guesswork. It is how modern intrusions unfold across nearly every incident Lares analyzes.
Attackers do not test “your perimeter.” They test the entire environment’s assumptions about identity, access, and trust.
A Typical Modern Attack Path
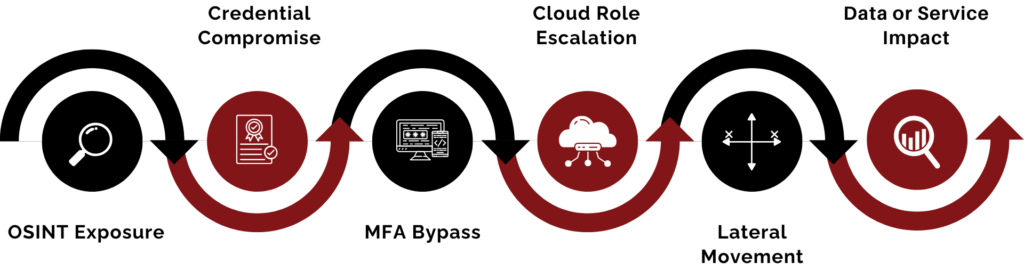
What CISOs Learn From Adversary Testing
Adversary testing is not a replacement for pentests. It is a different category of validation designed for a different outcome: understanding real-world resilience.
CISOs use adversary simulation to get answers that scoped assessments cannot provide:
-
How would an attacker progress in our environment
-
Which detections activate and which remain silent
-
What early signals defenders miss
-
Which paths expose business impact
-
Where identity and cloud drift undermine security
-
How fast attackers can escalate
-
What resilience looks like in practice
Adversary testing shows not just whether you are secure, but whether you stay secure under real conditions.
The Shift From Compliance to Resilience
Organizations no longer treat assessments as a checkbox. Boards ask CISOs to demonstrate readiness against real threats. Identity compromise, cloud escalation, and vendor access are no longer edge cases. They are the primary paths adversaries use.
Adversary testing is how you measure the performance of a security program, not the presence of one.
If you want to see an example of how Lares conducts adversary testing across identity, cloud, and detection layers, we are happy to share more.
Empowering Organizations to Maximize Their Security Potential.
Lares is a security consulting firm that helps companies secure electronic, physical, intellectual, and financial assets through a unique blend of assessment, testing, and coaching since 2008.
16+ Years
In business
600+
Customers worldwide
4,500+
Engagements
