About Lares
Lares® (Lar-Res) is a Denver, CO cybersecurity consulting company that prides itself on its ability to provide continuous defensive improvement through adversarial simulation and collaboration. Lares can help your organization validate its security posture through offensive security-focused services such as complex adversarial simulations, network penetration testing, application security assessments, insider threat assessments, vulnerability research, continuous security testing, virtual Chief Information Security Officer (CISO) services, and coaching.
Here at Lares, we want to help you make the most informed security decisions you can for your organization by giving you confidence. Confidence to defend against attackers with the tools at hand, address security and compliance concerns, and pass audits and assessments.
What is a Chief Information Security Officer?
A Chief Information Security Officer, or CISO, is an executive-level company officer or designated security leader within an organization. Depending on the organization, this individual might also be referred to as the Chief Security Officer (CSO), Head of Security, or Vice President (VP/SVP) of Security. What makes the CISO role, however, is the responsibilities of the office.
They are often responsible for the creation, implementation, enforcement, and measurement of an organization’s information security or cybersecurity program.
What is an ISO or BISO?
An Information Security Officer (ISO) is an individual, or group of individuals, responsible for certain aspects of security for an organization. Larger organizations will have individuals allocated to various aspects of the security program and those people are typically “members of” the Information Security Office. Similarly, a Business Information Security Officer (BISO) is an individual assigned to provide security leadership for one particular business unit, group, or team within the greater organization.
What is a Deputy CISO?
A Deputy CISO is responsible for portions of the organization’s information security program, under the leadership of a centralized CISO. In larger organizations, the security, risk, and compliance management aspects are simply too much for one CISO to manage. Deputy CISO’s ease that burden by compartmentalizing regional or other functional leadership tasks and assigning their success to localized or focussed resources.
What is a CSO?
A Chief Security Officer (CSO) is often used by an organization as an alternative name for a CISO. In other organizations, however, the CSO may have more responsibilities beyond information or IT security, such as physical security, asset security, and personnel security.
What is a Virtual or Fractional CISO?
A Virtual CISO (vCISO) or Fractional CISO is a retained board-level resource that can virtually sit inside the company and manage the security strategy, budget, and success of security, risk, and regulatory programs. They are not full-time employees, but rather, retained or on-demand resources that the company can rely on to help lead security.
What does CISO-as-a-Service Mean?
CISO-as-a-Service plays off the Software-as-a-Service (SaaS) acronym by offering senior security resources in an on-demand or as-needed basis. This retainer-level service typically assigned a CISO to multiple customers to manage the security of the client’s organization.
How do I pronounce CISO?
Like many things in information technology, there is no clear guidance on how to pronounce the CISO acronym. We’ve heard SEE-So, SIS-o, SIZ-o, and everything in between. To err on the side of caution, it may be best to just spell out the acronym as C-I-S-O until you learn how your organization, peers, and direct reports tend to refer to the role.
Who was the first CISO?
Steve Katz is widely known in security circles as the very first CISO and started his lifelong career in security with an internal consulting group at Citi Bank in the 1970’s. As the former senior security executive for Citibank/Citigroup, JP Morgan, and most recently Merrill Lynch, he states “I got my start in this business way before there was cybersecurity, and way before there was anything.”
Who was the first Federal CISO?
The office of the Federal Chief Information Security Officer of the United States was created on September 8, 2016. The role was created to guide cybersecurity policy, planning, and implementation in the U.S. Federal Government. The first appointment to this position was Brigadier General Gregory (Greg) J. Touhill, who stepped down in January, 2017 and was replaced by Grant Schneider (formerly the Deputy CISO). The federal CISO chairs the CISO Council, which allows collaboration across agencies on issues like identity management and vulnerability response.
Who was the first female CISO?
Unfortunately, there is no general consensus on who the first woman CISO in the industry was. A great resource that showcases some of the great women in the role, however, can be read here.
How do you become a CISO?
What skills should a CISO have?
An effective CISO needs to be able to balance the security of the organization with the requirements of the business. Individuals that enter the role thinking that it will be a hands-on, highly technical job will be quickly disappointed. The most successful CISOs put the requirements of the business first and work towards interweaving security to keep the organization safe, secure, and compliant with State, Federal, and International regulations.
As such, an individual that can balance security and business skills should be highly successful in the role.
Are there any formal CISO degrees available?
At this time there are no formal college or university degree programs specifically tailored to becoming a CISO. There are, however, a number of schools that offer information security, information assurance, and cyber security Associate, Bachelor, Graduate, and PhD degree programs. Though these degrees do not anoint you as a CISO, they may help give you the baseline skills needed to grow into the role.
Are there any CISO industry certifications?
(ISC)² Certified Information Systems Security Professional (CISSP)
Certified Information Systems Security Professional (CISSP) is an independent information security certification granted by the International Information System Security Certification Consortium, also known as (ISC)².
The CISSP curriculum covers subject matter in a variety of Information Security topics. The CISSP examination is based on what (ISC)² terms the Common Body of Knowledge (or CBK). According to (ISC)², “the CISSP CBK is a taxonomy – a collection of topics relevant to information security professionals around the world. The CISSP CBK establishes a common framework of information security terms and principles that allow information security professionals worldwide to discuss, debate and resolve matters pertaining to the profession with a common understanding.”
The CISSP curriculum is divided into eight domains:
- Security and Risk Management
- Asset Security
- Security Architecture and Engineering
- Communication and Network Security
- Identity and Access Management (IAM)
- Security Assessment and Testing
- Security Operations
- Software Development Security
(ISC)² Information Systems Security Management Professional (CISSP-ISSMP)
Information Systems Security Management Professional (CISSP-ISSMP), is an advanced information security certification issued by (ISC)² that focuses on the management aspects of information security. The certification exam consists of 125 questions covering 6 domain areas:
- Leadership and Business Management
- Systems Lifecycle Management
- Risk Management
- Threat Intelligence and Incident Management
- Contingency Management
- Law, Ethics, and Security Compliance Management
ISACA Certified Information Systems Auditor (CISA)
Certified Information Systems Auditor (CISA) refers to a designation issued by the Information Systems Audit and Control Association (ISACA). The designation is the global standard for professionals who have a career in information systems, in particular, auditing, control, and security. CISA holders demonstrate to employers that they have the knowledge, technical skills, and proficiency to meet the dynamic challenges facing modern organizations.
ISACA Certified Information Security Manager (CISM)
Certified Information Security Manager (CISM) is an advanced certification from ISACA that provides validation for individuals who have demonstrated they possess the knowledge and experience required to develop and manage an enterprise information security program. The certification intended for information security managers, aspiring managers or IT consultants who support information security program management. It is accredited by ANSI under ISO/IEC 17024:2003.
ISACA Certified in Risk and Information Systems Control (CRISC)
The Certified in Risk and Information Systems Control (CRISC) certification is an enterprise risk management qualification, favoured by professionals looking to build upon their existing knowledge and experience of IT/Business risk, identification and implementation of information system controls.
The certification requires prerequisite skills such as the ability to manage the ongoing challenges of enterprise risk and to design risk based information system controls. CRISC is one of the foremost certifications which help particularly IT professionals prepare for real world threats, with appropriate tools to both evaluate and manage risk. The CRISC certification is widely seen as the go-to accreditation for experts in the field of risk and information systems controls or those looking to progress their careers in this area.
EC-Council’s Certified Chief Information Security Officer (CCISO)
The Certified Chief Information Security Officer (CCISO) certification bills itself as an “industry-leading program that recognizes the real-world experience necessary to succeed at the highest executive levels of information security.” There are three cognitive levels tested on the CCISO exam but only two tested on the EISM exam. These levels are Knowledge (the cognitive level of questions used to recall memorized facts), Application (the cognitive level of question sussed to identify the candidate’s ability to understand the application of a given concept), and Analysis (the cognitive level of questions used to identify the candidate’s ability to identify and resolve a problem given a series of variables and context).
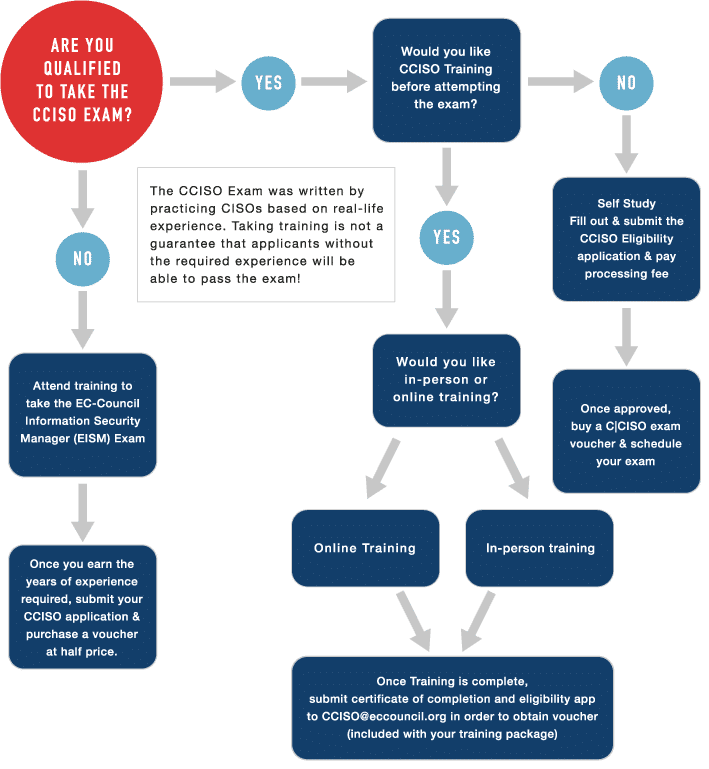
To find out if you are qualified to take the CCISO exam, EC-Council has provided a handy flow-chart to guide you.
What is the typical CISO reporting structure?
One of the most frequently asked questions is “who should the CISO report to”? Perhaps the easiest response is “to whoever allows them to be the most effective in their role.”
Common reporting structures have the CISO reporting directly to the Chief Executive Officer (CEO) or Chief Operating Officer (COO) but we’ve also seen CISO report into the IT hierarchy (to a Chief Information Officer or Chief Technology Officer), into Finance (Chief Financial Officer), and even Audit (Chief Risk Officer).
Can an organization have a CSO and a CISO?
Yes, larger organizations may feel the need to have both a CISO and a CSO to delineate responsibilities between technology security and physical/asset security. The CISO, however, does not necessarily need to report into the CSO, or vice versa, in order for both to be successful.
Who reports to the CISO?
As the de facto head of security, it’s very common for any and all “security” related roles to report into the CISO. This includes, but is not limited to security analysts, security engineers, incident response, digital forensics, threat intelligence, security research, and any other operational security roles you might imagine.
How much does a CISO typically make?
The typical CISO salary is entirely dependent on the geographic location of the organization, the experience of the individual, and the size of the company. According to Salary.com, the average CISO salary in the United States is $226,734 as of February 26, 2020, but the range typically falls between $198,127 and $261,745. Glassdor states that the average base pay for a CISO is $180,870 USD (as of March 31, 2020). ZipRecruiter claims that the CISO salary national average is $171,474.
Regardless of the posted averages and ranges, the role should pay as much as the company values security leadership within the organization.
How much does a Virtual CISO Cost?
A vCISO is typically billed out on an annual retainer basis for a set number of days or hours per year. It’s also common to see block hours of vCISO time to provide a “security backstop” for any issues that require security leadership as they arise. The actual hourly, daily, or project rate depends on the needs of the organization, the expected responsibilities, and the expertise provided by the vCISO.
How much can I save by using a Virtual CISO?
As the vCISO is a consultative resource, the organization is not required to pay them as they would a full time employee. As such, the organizational overhead is much lower than if the CISO were hired as an employee. Also, in our experience a full time CISO, like most full time employees, are not utilized at 100% of their capacity whereas a consultative resource is beholden to the tracking of time to the project.