About Lares
Lares® (Lar-Res) is a Denver, CO cybersecurity consulting company that prides itself on its ability to provide continuous defensive improvement through adversarial simulation and collaboration. Lares can help your organization validate its security posture through offensive security-focused services such as complex adversarial simulations, network penetration testing, application security assessments, insider threat assessments, vulnerability research, continuous security testing, virtual Chief Information Security Officer (CISO) services, and coaching.
Here at Lares, we want to help you make the most informed security decisions you can for your organization by giving you confidence. Confidence to defend against attackers with the tools at hand, address security and compliance concerns, and pass audits and assessments.
What is cloud security?
Cloud security refers to a broad set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing from external and insider cybersecurity threats. Cloud computing is the prevailing go-to-market strategy across private and public sectors for organizations seeking to obtain or keep market advantage. Bad actors have shifted tactics, techniques and tips in response to this technological shift in their ongoing pursuit of businesses globally.
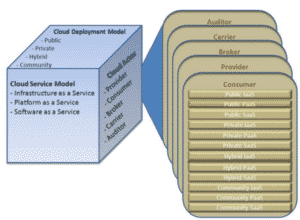
Cloud security and security management best practices are designed to attenuate attacker advantage and mitigate emerging threats to organizations and valued assets. Four deployment models public, private, hybrid and community clouds comprise the foundational cloud environments. Three service models Infrastructure, Platform, and Software service models (IaaS, PaaS, and SaaS, respectively) form the basis. The three major cloud providers are, Azure and Azure Active Directory, Google Cloud Platform (GCP), and Amazon Web Services (AWS).
What are the common cloud deployment models?
Public
Public clouds are multitenant environments with resources (hardware, software, facilities, and staff) owned and operated by a vendor and sold, leased, or rented to anyone. Multiple customers will share the underlying resources that are owned and operated by the provider.
Private
A private cloud is typified by resources dedicated to a single customer; no other customers will share the underlying resources (hardware and perhaps software). Therefore, private clouds are not multitenant environments.
Hybrid
Hybrid cloud is a composition of a public cloud and a private environment, such as a private cloud or on-premise resources, that remain distinct entities but are bound together. Gartner defines a hybrid cloud service as a combination of private, public and community cloud services, from different service providers. Hybrid cloud deployments extend the capacity or the capability of a cloud service, by aggregating and integrating cloud services.
Other
Other cloud deployment models worth mentioning are community and multi- cloud. Community cloud shares infrastructure between several organizations from a specific community with common concerns (security, compliance, jurisdiction, etc.), whether managed internally or by a third-party, and either hosted internally or externally. The costs are spread over fewer users than a public cloud (but more than a private cloud), so only some of the cost savings potential of cloud computing are realized.
Multi-cloud is the use of multiple cloud computing services in a single heterogeneous architecture to reduce reliance on single vendors, increase flexibility through choice, mitigate against disasters, etc. It differs from hybrid cloud in that it refers to multiple cloud services, rather than multiple deployment modes (public, private, legacy).
What are the cloud service models?
According to NIST publication 800-145, there are three types of foundational service models, Software as a Service (SaaS), Platform as a Service, and Infrastructure as a Service (IaaS).
SaaS
Software as a Service (SaaS) is a method of software delivery and licensing in which software is centrally hosted and accessed online via a subscription versus COTS software installed on computers. Sometimes referred to as “on-demand software”, SaaS was formerly “software plus services” by Microsoft.
PaaS
Platform as a Service (PaaS) abstracts and provides development or application platforms,such as databases, application platforms (e.g. a place to run Python, PHP, or other code), file storage and collaboration, or even proprietary application processing (such as machine learning, big data processing, or direct Application Programming Interfaces (API) access to features of a full SaaS application). The key differentiator is that, with PaaS, you don’t manage the underlying servers, networks, or other infrastructure.
In PaaS the cloud user only sees the platform, not the underlying infrastructure. In our example, the database expands (or contracts) as needed based on utilization, without the customer having to manage individual servers, networking, patches, etc.
IaaS
Infrastructure as a Service (IaaS) offers access to a resource pool of fundamental computing infrastructure, such as compute, network, or storage. Infrastructure as a service (IaaS) is the cloud model in which the cloud customer has the most responsibility and authority. The provider is responsible for the data center’s buildings and land, connectivity and power, and the hardware assets the customer’s programs and data will reside on. The customer, however, is in charge of everything from the operating system and up; all software will be installed and administered by the customer, and the customer will supply and manage all the data.
What are some examples of cloud security standards and frameworks?
- NIST 800-144 The NIST Definition of Cloud Computing
- NIST 800-145 Guidelines on Security and Privacy in Public Cloud Computing
- ISO 27017 Guidelines for security controls applicable to the provision and use of cloud services
- ISO 27018 Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
What are some examples of cloud security reference models?
Draft NIST 500-299 defines the current notional cloud security reference model.
What is the Cloud Security Alliance (CSA)?
The Cloud Security Alliance is a not-for-profit organization with the mission to “promote the use of best practices for providing security assurance within Cloud Computing, and to provide education on the uses of Cloud Computing to help secure all other forms of computing. The CSA’s mission to promote the use of best practices for providing security assurance within Cloud Computing, and to provide education on the uses of Cloud Computing to help secure all other forms of computing.
What types of roles exist in cloud computing?
- Cloud Security Architect – The Cloud Security Architect specialization focuses on planning, analyzing, designing, configuring, testing, implementing, maintaining, and supporting an organization’s on-premise and cloud security infrastructure.
- Cloud Security Engineer – The Cloud Security Engineer provides cyber security expertise in the analysis, assessment, development, and evaluation of security solutions and architectures to secure applications, operating systems, databases, and networks.
- Site Reliability Engineer – Site reliability engineers create a bridge between development and operations by applying a software engineering mindset to system administration topics.
What is the Certificate of Cloud Security Knowledge (CCSK)?
Issued by the CSA, CCSK is a widely recognized standard of expertise for cloud security, providing the necessary foundations to secure data in the cloud. The CCSK body of knowledge consists of the fourteen CSA domains and two special domains, the Cloud controls matrix (CCM) and the European network and information security agency (ENISA).
What is the Cloud Certified Security Practitioner (CCSP) Certification?
The official (ISC)² Cloud Certified Security (CCSP) certification indicates that its holder possesses the technical skills and knowledge to design, manage and secure data, applications and infrastructure in the cloud using best practices, policies and procedure. The certification is intended for experienced cloud professionals who have a minimum of five years of experience in the industry with three of those years being in information security and one year in one of the six CCSP domains.
- Cloud Concepts, Architecture, and Design
- Cloud Data Security
- Cloud Platform and Infrastructure Security
- Cloud Application Security
- Cloud Security Operations
- Legal Risk And Compliance
What is the Professional Cloud Security Manager Certification?
Professional Cloud Security Manager – Provider: EXIN, the Cloud Credential Council’s Professional Cloud Security Manager certification program prepares IT professionals for security, risk, and compliance issues as they relate to cloud computing. Specifically, the program focuses on the intersection between business and technical security challenges in an enterprise’s cloud computing environment. Technically, there are no prerequisites for IT professionals to apply for the exam. However, the Cloud Credential Council recommends that interested parties enter the program with five years of working experience in enterprise security along with a deep understanding of cloud computing services and deployment models.
What is the Cloud Integrator Secure Cloud Certification?
Certified Integrator Secure Cloud Services – Provider: EXIN, a Dutch certifier of IT professionals worldwide, encourages its students to take an integrated approach to IT issues and challenges. As such, those who become a Certified Integrator Secure Cloud Services do so free of cost by combining the following foundational certificates: IT service management, information security, and cloud computing. Each of those foundational certificates costs 155 USD. Professionals do have some flexibility when it comes to qualifying for this integrated certificate, however. For example, they can swap the EXIN IT service management certificate out for an alternative accreditation offered by ITIL or MOF. They can also replace EXIN cloud computing with the Cloud Technology Associate certification offered by the Cloud Credential Council.
What is the CompTIA Cloud+ Certification?
CompTIA Cloud+ – Provider: The Computing Technology Industry Association (CompTIA), a non-profit trade association, offers its globally recognized, accredited, and ISO 17024-compliant Cloud+ certificate to practitioners who wish to validate their knowledge, skills, and abilities in implementing and maintaining cloud technologies. The program teaches students key issues associated with the cloud including models, virtualization, infrastructure, resource management, business continuity, and security. CompTIA recommends that those who register for the exam possess at least 2-3 years’ experience in networking, storage, or IT data center administration as well as familiarity with at least one of the major hypervisor technologies for server virtualization.
What are the top cloud security concerns of cloud consumers?
We understand the complexity of security problems our customers face because we face them too. For most cloud consumers, delineating cloud responsibility and accountability between themselves and cloud providers is top of mind. The standing mantra holds: the cloud provider is responsible for security of the cloud (infrastructure) while the cloud consumer is responsible for security in the cloud (data). While cloud adopters become more at ease with cloud migration, according to the cloud security insiders 2019 release of their annual report, nearly 93% of cloud customers/consumers are moderate to extremely concerned about “security of the cloud.” 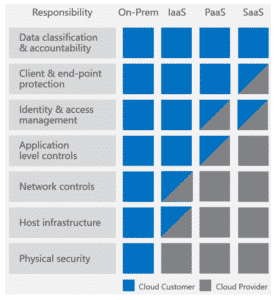 Conversely, “security in the cloud” concerns about data leakage and data privacy weigh heavy on the minds of two-thirds of the survey’s respondents. Exposed data, malware infections, exploited vulnerabilities and account compromise are additional concerns of security stakeholders. Cloud consumers are constantly faced with maintaining a delicate balance around clearly defined responsibilities in the cloud. Our assessment services help bring clarity to the lines of delineation between the cloud provider and our clients. More importantly, we identify gaps that could be exploited to enhance a customer’s security in the cloud.
Conversely, “security in the cloud” concerns about data leakage and data privacy weigh heavy on the minds of two-thirds of the survey’s respondents. Exposed data, malware infections, exploited vulnerabilities and account compromise are additional concerns of security stakeholders. Cloud consumers are constantly faced with maintaining a delicate balance around clearly defined responsibilities in the cloud. Our assessment services help bring clarity to the lines of delineation between the cloud provider and our clients. More importantly, we identify gaps that could be exploited to enhance a customer’s security in the cloud.
What is cloud workload security?
Cloud Workload Security is achieved by solutions that discover, monitor, and secure the code artifacts and applications and associated accounts, storage instances, and control planes deployed on cloud infrastructure.
What is the CSA Cloud Security Guidance?
The Security Guidance for Critical Areas of Focus in Cloud Computing v4.0 guide published by the CSA defines 14 domains about critical areas of concern regarding the security of cloud assets. The security guidance supports cloud adoption efforts providing prudent advice for businesses managing and mitigating risks associated with migration of legacy environments. The guidance consists of fourteen domains ranging from cloud computing and architecture references to application, data security and identity management.
Domain 1 – Cloud Computing Concepts and Architectures
Domain 1 is concerned with the various cloud computing models, where responsibility for security provisions lies, and how each is to be protected. For the purposes of the CSA Guidance, cloud architecture is defined in terms of Software as a Service (e.g. Salesforce or Office 365), Platform as a Service (e.g. Windows Azure or Heroku), and Infrastructure as a Service (e.g. Amazon AWS or Microsoft Azure).
The Domain then goes on to describe a high-level process that can be used as a model for managing cloud security:
- Identify necessary security and compliance requirements, and any existing controls
- Select your cloud provider, service, and deployment models.
- Define the architecture
- Assess the security controls
- Identify gaps in those security controls
- Design and implement controls to fill the gaps
- Manage changes over time
Domain 2 – Governance and Enterprise Risk Management
Domain 2 explains how the issues of governance and risk management change under the cloud computing model, not least because the cloud provider introduces a third party into the process. To assist with improving governance, the CSA highlights the following tools:
- Contracts that clearly split responsibilities between the cloud provider and customer
- Supplier assessments performed by the customer to verify the suitability of the provider
- Compliance reporting that ensures cloud provider security processes and protections align with the customers
When dealing with cloud technologies, enterprise risk management works on the principle of shared responsibilities. The ultimate responsibility for security remains with the client, but the provider will accept some as part of their service; these will vary according to the cloud deployment model, public, private or hybrid. To assist, the CSA has produced a basic supplier assessment:
- Acquire documentation from the provider.
- Review their security program and documentation.
- Review any legal, regulatory, contractual, and jurisdictional requirements that apply to supplier and customer.
- Evaluate the contracted service in the context of your information assets.
- Evaluate the provider as a whole, including factors such as finances/stability, reputation, and outsourcers.
Domain 3 – Legal Issues, Contracts, and Electronic Discovery
Moving data to the cloud creates several potential issues regarding data protection, sovereignty and the legal implications of sending data between jurisdictions. Cloud adopters must ensure that their deployments fully comply with all relevant legislation to avoid prosecution.
Customers must be familiar with the relevant legislation that applies to their installation. They also need to ensure that service contracts clearly delineate responsibilities between parties. Due diligence testing becomes a regular routine as companies continually assess and confirm compliance. They must also ensure that data is retained correctly in relation to electronic discovery for use in both civil and criminal investigations and court cases.
Domain 4 – Compliance and Audit Management
With the legal issues understood, Domain 4 is concerned with businesses achieving – and maintaining – compliance. As with understanding, compliance remains the responsibility of the client, even when using systems hosted in the cloud.
Proving compliance in the cloud is a two-stage process, first auditing the provider against each regulation or standard. The customer’s apps and services built on top of the provider’s platform must also be assessed. The CSA describes this as a pass-through audit.
Domain 4 concludes with advice relating to audit management. As well as retaining the services of a third party to carry out the audits, cloud users are reminded of the importance of instituting a program of continuous assessment.
Domain 5 – Information Governance
Information governance relates to how data is used. The official CSA definition states: ‘Ensuring the use of data and information complies with organizational policies, standards and strategy — including regulatory, contractual and business objectives.’
The cloud operating model introduces a third party into the governance model. To address this complexity, Domain 5 outlines nine specific areas of interest that businesses should address as they draw up their information governance strategy:
- Information Classification
- Information Management Policies
- Location and Jurisdiction Policies
- Authorizations
- Ownership
- Custodianship
- Privacy
- Contractual controls
- Security controls
Domain 5 also describes a six-phase data security lifecycle, covering every stage between creation and destruction. These are:
- Creation
- Storage
- Use
- Sharing
- Archiving
- Destruction
Domain 6 – Management Plane and Business Continuity
The term ‘management plane’ describes the tools and interfaces used to manage infrastructure, platforms and applications – both onsite and in the cloud. Securing these tools against unauthorized access is critical to protecting systems from being exploited by hackers. The CSA recommends following best-practice principles of limiting access permissions to only what is strictly required, for both human operators and automated services.
Cloud platforms are designed to fail-over automatically in the event of an outage, but the customer remains responsible for protecting their data against loss. The CSA recommends building a multi-level business continuity plan that covers data loss/outages including:
- Data stored in their hosted environment
- A total loss of service from their provider
- Provisions for a private cloud failure
Domain 7 – Infrastructure Security
There are two (main) layers of infrastructure to consider in cloud environments: the physical systems and the abstracted application/data layer. To provide virtualization and failover capabilities, the hosted environment makes heavy use of virtual networks (software-defined security – SDSec).
Addressing the two layers of infrastructure requires further examination of:
- Network functionality, such as the use of SDSec to increase separation and impact of a breach
- Network configuration to limit and restrict access to authorized users acting within the limits of their permissions
- Building immutable workloads to secure data against common threats
- Leverage log analysis to detect suspicious behavior and to trigger the required recovery protocols (when required)
Domain 8 – Virtualization and Containers
Virtualization is fundamental to cloud operations, abstracting data and applications from the underlying hardware platform. The CSA has identified two new layers requiring security controls: the virtualization technology itself (typically the hypervisor) and the virtual assets.
When designing security protocols, cloud users must define responsibilities for provider and customer in the following areas:
- Virtualized compute, such as the virtual machines themselves
- Virtualized network resources, including monitoring and filtering. Attention is also drawn to ‘cloud overlay networks’ that link multiple cloud services
- Storage, and how information is held within the virtualized environment
- Software containers, and the use of service and security isolation can be employed to prevent data leakage or theft
Domain 9 – Incident Response
Security breaches are (statistically speaking) a certainty, which means defining an incident response plan is vital to help limit fallout. Domain 9 references a four-stage incident response lifecycle to help identify the various phases of a good plan:
- Preparation – building a response capability in advance of a security incident
- Detection and analysis – deploying tools, systems, and procedures to identify potential breaches, risks, and threats
- Containment, eradication, and recovery – limiting the impact of a breach, removing the threat, and restoring normal operations
- Post-mortem – analysis of the response, and improving future operations based on those observations
Service customers will need to carefully consider the available tools, logs and reports, and the role their cloud provider will play in incident response.
Domain 10 – Application Security
The CSA identifies three major areas for a successful application security program:
- The Secure Software Development Lifecycle (SSDLC) that makes security a critical concern at every stage of the application development process
- Integrate security into application design and architecture
- Build a DevOps / Continuous Deployment (CD) capability to push through security updates, patches and fixes quickly and efficiently
Domain 11 – Data Security and Encryption
Data stored in the cloud must be secured appropriately through measures such as:
- Storing data in the most appropriate location
- Protecting data held in the cloud using access controls, encryption and architecture design
- Monitoring and reporting on data activities
- Enforcing these measures in line with compliance requirements
As well as dealing with data already in the cloud, Domain 11 documents measures to protect the information in transit, particularly during upload. The CSA also emphasizes the importance of using data storage security measures offered by the cloud provider including at-rest encryption and tokenization.
Domain 12 – Identity, Entitlement and Access Management
Restricting access to stored data has always been complicated, but the cloud adds an additional layer of complexity. The systems used to control access to resources are now shared between user and cloud provider for instance.
Domain 12 defines Identity and Access Management as “the security discipline that enables the right individuals to access the right resources at the right times for the right reasons.” To achieve this goal, the CSA recommends the use of technologies like:
- Security Assertion Markup Language (SAML), an XML-based identity management standard that supports authentication and authorization
- OAuth, an HTTP framework for delegating access control between services
- OpenID, a federated authentication service that uses HTTP and URLs to verify user identity
- The eXtensible Access Control Markup Language (XACML) standard for defining access controls – typically used in conjunction with SAML and OAuth
- The System for Cross-domain Identity Management (SCIM) standard exchanges identity information between domains
Domain 13 – Security as a Service
Security as a Service (SecaaS) typically describes security products or services that are delivered from the cloud. They typically exhibit the same characteristics as other cloud services described in Domain 1.
Domain 13 identifies 13 SecaaS categories:
- Identity, Entitlement, and Access Management Services – including Federated Identity Brokers
- Cloud Access and Security Brokers (CASB, also known as Cloud Security Gateways) – like Microsoft Cloud App Security
- Web Security (Web Security Gateways) – such as anti-malware content filters
- Email Security – like anti-spam filters and phishing detection systems
- Security Assessment – systems that audit cloud deployments and on-site infrastructure
- Web Application Firewalls – that redirect and filter DNS traffic to identify and block malicious activity
- Intrusion Detection / Prevention (IDS / IPS) – that use heuristic monitoring to identify and block suspicious network activity
- Security Information & Event Management (SIEM) – to aggregate and analyze event logs from multiple sources in real-time
- Encryption and Key Management – services that encrypt data and manage decryption keys, typically used to protect information held in SaaS platforms.
- Business Continuity and Disaster Recovery – that helps to protect corporate data against loss from cloud storage
- Security Management – services that combine multiple traditional security measures that includes antivirus, mobile device management, network security, etc.
- Distributed Denial of Service Protection – services that reroute network traffic to block or mitigate DDoS attacks.
Domain 14 – Related Technologies
The final CSA domain discusses technologies that are reliant on cloud services to operate, or are typically only seen in cloud environments. Domain 14 lists four such technologies:
- Big Data – applications that use vast, unstructured datasets that need to be processed in real-time
- Internet of Things (IoT) – applications that collate, process and analyze data streamed from a potentially vast array of sensors
- Mobile computing deployments – that use the cloud to simplify management and device security
- Serverless computing models – that rely on PaaS to deliver containerized services and applications
What is the Cloud Control Matrix?
The CSA Cloud Controls Matrix (CCM) is a cybersecurity control framework for cloud computing, composed of 133 control objectives that are structured in 16 domains covering all key aspects of the cloud technology. It can be used as a tool for the systematic assessment of a cloud implementation, and provides guidance on which security controls should be implemented by which actor within the cloud supply chain.
What is a cloud security assessment?
A Cloud assessment encompasses reviews of systems using appliances, software agents, network and application vulnerability assessments, and penetration testing to determine risks in deployments and services.
What is a Cloud Assessment Methodology?
The ability to test services deployed in Azure, GCP, and AWS, varies on permissions of the cloud provider, service models and available tools and methods at the disposal of the assessor. The CSA has recently published a cloud penetration playbook in which a consensus testing methodology is outlined. Example tactics, techniques, and procedures (TTPs) include:
- Sophisticated attack methodology
- Enumeration
- Credential theft and account takeover
- Access privilege escalation
- Persistence
- Specialized chained attacks cloud attack simulation.
Our objective regardless of technology is to identify and protect. We focus our attention on
- Unauthorized Access (e.g., steal credentials, account takeover)
- Insecure interfaces/APIs
- Misconfiguration items (e.g. leaky buckets)
- Insider Threat
- Weak Control Plane
- Abuse of cloud services
What are the top cloud threats?
The Cloud Security Alliance top cloud threats released annually. Underlying the ratings are threat modeling (STRIDE), the CSA Security Guidance (14 domains), and the CSA Cloud Control Matrix (CCM) Controls. The Cloud Top Threat WG risk ranks each threat against 4 criteria: history of ranking, security responsibility, architecture, and cloud service model. Anecdotal stories and examples are provided with each threat as supporting evidence for the rating.
What is a cloud security penetration test?
Security testing of cloud based systems, environments and services is nuanced and unique to the public cloud . Security in the cloud is tested, not security of the cloud.
In the fundamental sense the principles of penetration are the same as any others, simulating real world attacks with hopes of understanding the TTPs of adversaries. Insights gained during testing can help organizations better defend themselves.
Security controls that fall under the complete responsibility of the Cloud Service Provider (CSP) are usually not within the scope of a penetration test that is commissioned by the cloud consumer. For example, in a Software as a Service (SaaS) environment, it is within the penetration tester’s scope of authority to exploit excessive permissions given to a particular user to conduct business level attacks (i.e. approve expenditure). However, the tester should not test the implementation of access control (session validation) or the SaaS application input filtering (i.e. SQL injection) in the SaaS application. This is because the test involves compromising underlying infrastructure that is out of the scope of authority of the recipient of the penetration test. Therefore, underlying infrastructure is normally not part of the scope of a penetration test unless explicit permission from the CSP is given.
The scope for testing and application of test cases also differs from service model to service model. For SaaS applications, the scope is small. With IaaS logically the scope is expanded. Security of the cloud components are potential targets in scoping if the cloud service provider is in agreement.
How do I get permission to test deployments in Microsoft Azure?
Beyond scoping and gaining permission to assess a given cloud target, testers must notify cloud providers before penetration activities commence. You can submit a notice of testing directly on the Microsoft notification page. Microsoft also provides rules of engagement.
How do I get permission to test deployments in AWS?
Guidelines for testing anything associated with Amazon Web Services are listed on their rules portal.
How do I get permission to test deployments in GCP?
GCP has no particular guidelines pertaining to testing cloud platform infrastructure other than the following: If you plan to evaluate the security of your Cloud Platform infrastructure with penetration testing, you are not required to contact us. You will have to abide by the Cloud Platform Acceptable Use Policy and Terms of Service, and ensure that your tests only affect your projects (and not other customers’ applications). If a vulnerability is found, please report it via the Vulnerability Reward Program.

