The Gathering of the Vulnerability Wranglers 2.0 (VW 2.0) panel debuts today on InfoSecWorld’s 2020 Digital event. As a content leadership advisor for InfoSecWorld USA, I have had the pleasure of hosting and moderating the panel for the two years and becoming a staple of the event. Our cast of wranglers (i.e., researchers and thought leaders), Alex Moss, CEO, Conventus, Adrian Sanabria, Advocate at Thinkst Applied Research, Jake Kouns, CEO Risk Based Security, and Jonathan Cran, Director of Research at Kenna Security have come together for more friendly wrangling and banter. The panel reflects on #AllThingsVulnerabilities and what’s transpired over the past year. Unsurprisingly, each panelist echos the sentiment that much in the world has changed since we last met. What is unchanged is the unrelenting growth rate of which vulnerabilities.
2020 Vulnerability Management Issues
As the art of vulnerability wrangling continues to evolve to meet the challenge of wrangling at scale, top of mind for the panel discussion are the following talking points:
- What are the significant vulnerability events in the past year?
- With vulnerabilities increasingly rising, practitioners, vendors, and researchers are examining more closely the efficacy of the various methods (e.g., updating of the CVSS, the release of the EPSS, etc.) to wrangle them. Are we any better off a year later?
- How are we doing with patching? Is patching too hard given the complexity of infrastructures and the ever-expanding attack surface? Can we rely on:
- Risk-based approaches to vulnerability management consume the current vulnerability management marketplace. Haven’t we been discussing ‘risk’ approaches for a decade or more within our industry? Should we be taking more cues from risk management models outside of our space?
- Predictions for the coming year? What’s next?
What’s Ahead: Focus on The Attack Surface
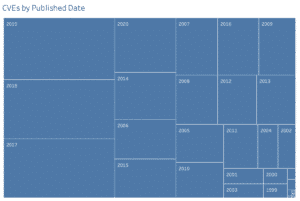
And we do have predictions. Kouns says vulnerability practitioners potentially face a “rough year” ahead as an impending vulnerability Fujiwharas loom in 2020. Although that may be, Cran suggests that year over year (YoY), for three consecutive years, vulnerability totals have remained consistent.
Sanabria and Moss say that all organizations need to enhance their capabilities to understand the scope of their attack surfaces ahead of colliding vulnerability events. Dan Geer has argued that the attack surface continues to grow at a rate that far outpaces our ability to perform proper due diligence, which is not the failure of care by organizations. Private and public sectors cannot act fast enough. Our panel dives into this very issue of wrangling quicker. Wrangling faster.
Defining Vulnerability Wrangling, Building Collaboration
Vulnerability wrangling is best defined as “intelligence, prioritization, and remediation,” according to Kouns. His co-panelists generally agreed. While prioritization and remediation consume teams, the intelligence of the attack surface requires more considerable attention. Further, gathering data is not the sole responsibility of one group. The knowledge of one’s attack surface involves collaboration. It’s not just IT’s job or security’s responsibility to gather intelligence. A truly collaborative effort helps organizations manage vulnerability issues ahead of threats is the core takeaway of VW 2.0. On the Lares blog, we often talk about pentest, red, and purple teaming our core strengths. Our engagements are not what they are without a deep understanding of the attack surfaces of our clients.
Conclusion of VW 2.0
To wrangle vulnerabilities requires intelligence collection and breadth of collaboration. Most importantly, there is hope. Things are getting better as collaboration within and outside of our industries strengthen our methodologies to secure our industries and assets and keep our consumers safe.

Mark Arnold has a 15+ cybersecurity career, serving 8 of those years in leadership roles. As a transformational leader, Mark has built security teams and programs, authored maturity model blueprints to optimize risk management processes, and implemented security domain practices at large enterprises and service providers. Mark’s areas of interest include cloud security, threat intelligence, and vulnerability research, nation-state attack methods and related activities (e.g. information operations and disinformation campaigns) and their collective impact on nations and society. Mark recently completed an executive education cohort on the intersection of cybersecurity and technology at Harvard’s Kennedy School.