How to Scope Your Next (or First) Pentest
The following blog post summarizes some of the key points from the first extracted session of the inaugural Lares Customer Summit that took place on Wednesday, December 2nd, 2020. We hope you enjoy the excerpted highlights from Tim McGuffin’s (Director of Adversarial Engineering) session on helping clients identify the appropriate type of assessment and coverage for their pentesting needs. The extracted session is available at the bottom of the page.
Pentest Scoping is Not Just a Checklist
Getting ready for pentesting services with Lares is less about project scoping questions and preparing clients for a journey of continuous improvement – a journey to maturity. Our testing services path is marked by four phases, using frameworks as guideposts towards an improved security posture.
The journey starts by mapping our services to the NIST CSF, a common and comprehensive framework (Note – clients are encouraged to choose an appropriate framework for their organization). The NIST CSF lifecycle starts with Identifying and curating an inventory of your assets and data residence. Next, organizations focus on protective controls to prevent attacks that they can predict. Organizations then test the detective capabilities of their controls, remediating any gaps in coverage. Finally, teams determine their ability to respond (if an attack is detected) and validate business resilience should an attack occur. To this end, we champion a multiyear pentesting roadmap for clients that result in coverage across the NIST CSF.
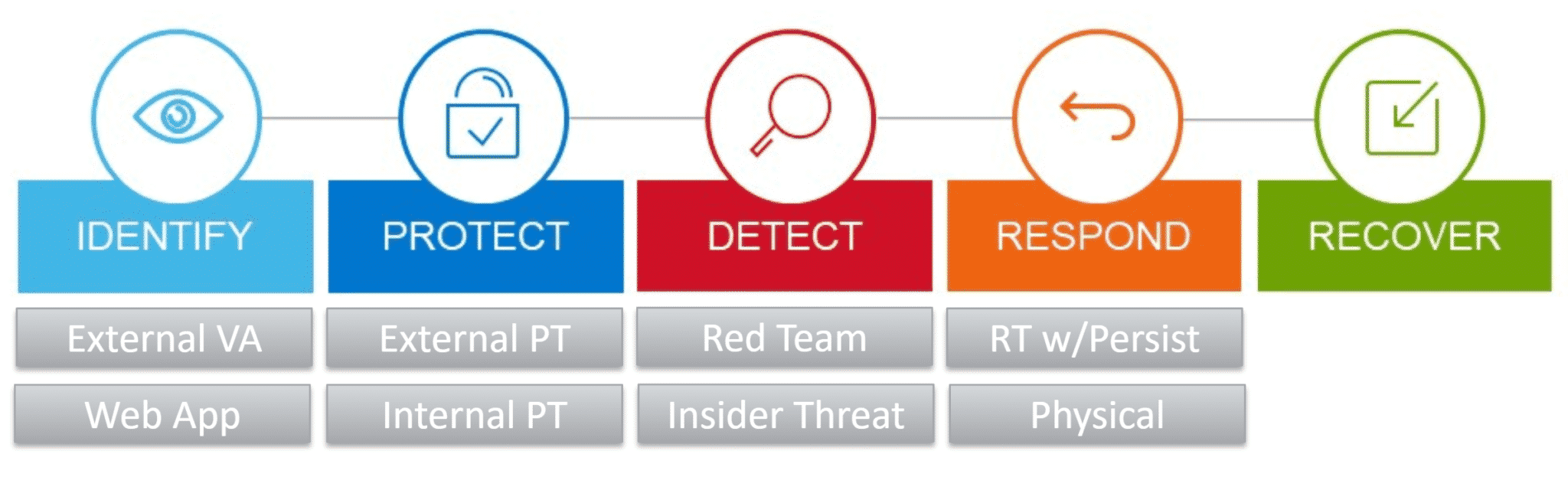
To reiterate and clarify further, Lares advocates a structured pentesting program to build organizational maturity against the NIST CSF. We map our prescriptive services to the NIST CSF functions as follows: Lares External vulnerability assessment & web application mapped to Identify; External/Internal pentest (e.g., Do your controls work) to Protect; Red Team and Insider Threat (e.g., gained a foothold) to Detect; Full-scope, Red Team with persistence, Purple Team to Respond.
First Steps
Just starting? We recommend that our clients undergo an external vulnerability assessment (EVA) and web application assessment. These services provide clients an internet-based view of exposed vulnerabilities to untrusted networks and threat actors. An EVA is a validation of external/perimeter security controls, patching firewall, and asset management controls (i.e., what does the client environment look like?). We call the EVA a light touch assessment. We attempt to identify anything known about the target client – IP addresses, domain names, networks, etc. through enumeration. If we determine vulnerabilities, we will try to validate and report them to the client. We then ask the client to review discovered assets, purported vulnerabilities, and internal processes (e.g., validate whether vulnerability scanning is working).
The Web Application Assessment (WAA) is recommended for any target applications exposed to the internet or uncommon services using manual and automated methods to discover common and uncommon vulnerabilities
Next Step: Testing Controls that Prevent Attacks
External and internal pentests are intended to ensure controls are protecting the client organization as expected. This phase of testing is essentially a validation of the client’s perimeter preventive controls (patching, intrusion detection systems (IDS), multi-factor authentication (MFA, access controls) from “threats across the internet.” Akin to the previous step, we seek to know “what infrastructure the client believes they own.” External pentesters from Lares curate discovered findings, so clients can remediate issues, mitigate existing threats, and enhance detection capabilities. And spend time abusing authentication portals (e.g., we look for single factor services, MFA bypass). We cannot emphasize enough that clients take the time to review discovered exploit paths to improve preventative controls at this stage.
The companion service, internal pentesting, simulates threat actors that have obtained a foothold in the network via external means. An internal test assumes a physical breach and a successful bypass of physical controls. The simulation includes bypassing external controls, uncovering exploits, and discovering credentials and novel legacy systems.
By Any Means Necessary
Once a client has a good handle on preventing attacks and achieved a good security posture and validated detective measures, a full scope assessment is needed. At this stage, we apply a holistic approach to validate a client’s information security posture. Testing at this stage is less concerned with networks, computers, and IP addresses on the wire (i.e., IT security) and more laser-focused on vetting people process technology (i.e., information security). In assessing a client’s Information security posture, we focus our efforts on electric, physical (e.g., B&E), and social (e.g., exploiting people & social engineering) components. We want to determine how teams fare against these adversarial simulations to boost and build defensive confidence.
At this stage, clients understand, “We’re going to try to get in,” given enough time. We are going to be “slow and stealthy.” We will collaborate and leverage multiple sources of information to string together compound attacks to compromise our client targets. After a full scope engagement, we ask that clients review technology, review preventive controls, and remediate gaps in detective measures (e.g., camera locations, card access system modification, employee training).
Susceptible to Insider Threats?
Testing the client’s ability to detect insider threats are also vetted at this stage. Clients provision our testers as standard employees with a standard provisioned asset and access. With that level of access, we determine what we can achieve in the environment by living off the land (i.e., using tools available in the environment). We will attempt to escalate by abusing privileged access management (PAM) controls or authentication with hopes of exfiltrating sensitive data or other information assets.
We Get to Play Dungeon Master
The last phase of testing is the Red Team with persistence service. We get to play dungeon master and operate like an attacker in a client network. The client gets to execute its IRP. We are essentially engaged in “live sparring” with the client, playing offense to their defense. We are going to live in the client network until time runs out or the client eradicates us. Along the way, our team will provide defensive tips and insights to enhance client detective and response capabilities. The client exits the engagement, having tuned processes, and experienced adversarial collaboration (see Purple Teaming with Lares). Although we enter this stage as the dungeon master, the clients emerge as worthy defenders of their infrastructures.
The parallel assessment at this stage of the journey is a full-on physical assessment. We attempt to learn as much as we can about an organization’s people. The possibilities are endless. Having breached physical access, we might rifle thru files to gather as much information as possible about our client target. We will surveil people, obtain covert entry, and/or socially engineer an entrance into the building to show clients what is physically possible.
Takeaways
I am biased when I state that our penetration testing services catalog is one of the most comprehensive. Few have clearly laid out the rationale for pentesting as-a-journey in the manner that Tim has here. Be sure to listen to the entire audio for his exceptional insights on this subject matter – Cheers.
Watch The Session

Mark Arnold has a 15+ cybersecurity career, serving 8 of those years in leadership roles. As a transformational leader, Mark has built security teams and programs, authored maturity model blueprints to optimize risk management processes, and implemented security domain practices at large enterprises and service providers. Mark’s areas of interest include cloud security, threat intelligence, and vulnerability research, nation-state attack methods and related activities (e.g. information operations and disinformation campaigns) and their collective impact on nations and society. Mark recently completed an executive education cohort on the intersection of cybersecurity and technology at Harvard’s Kennedy School.