Another year has passed and that means that it’s time for the annual Verizon Data Breach Investigations Report (DBIR). In its 13th year, the DBIR provides data from real-world breaches that are analyzed by the team at Verizon. In an effort to enrich their data set, the Verizon team relies upon trusted contributors with access to meaningful data. For the 5th year in a row, Lares has been one of those trusted partners and continues to provide data resulting from our metric phishing and targeted black box spear-phishing engagements.
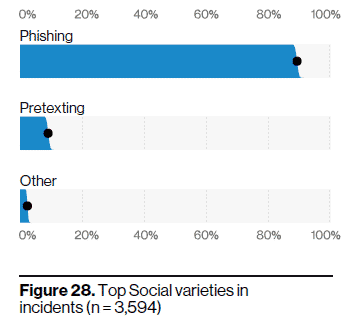
“Phishing is the top action highlighted within the 2020 DBIR. Lares Consulting’s contribution to our phishing data corpus was used throughout the report, including in the section on Social actions as well as in the individual industries,” said Gabriel Bassett, Data Scientist and DBIR Co-author. “We greatly appreciate its contribution and look forward to continued collaboration!”
The DBIR’s malware findings “further reinforce the trends of phishing and obtaining credentials with regards to breaches,” claims the report, and malicious links embedded within phishing emails takes the top spot as the number one malware vector in breaches.
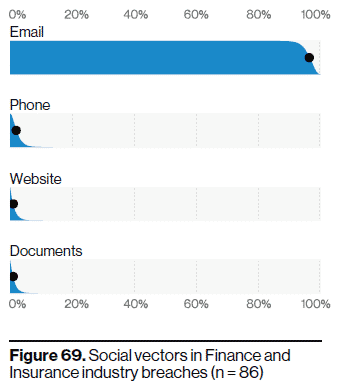
Social actions, including Phishing and Pretexting, arrived via email 96% of the time, while only 3% arrived through a website. “A little over 1% were associated with Phone or SMS, which is similar to the amount found in Documents,” claim the authors.
“While credentials are by far the most common attribute compromised in phishing breaches,” says the report, “Phishing has been (and still remains) a fruitful method for attackers.”
One notable finding in the report is that cyber-espionage, consisting of espionage, enabled via unauthorized network or system access, and largely constitutes nation-states or state-affiliated actors, rely heavily on Social and Malware combined vectors. In fact, Phishing was used in 81% of the incidents and some form of malware in 92%.
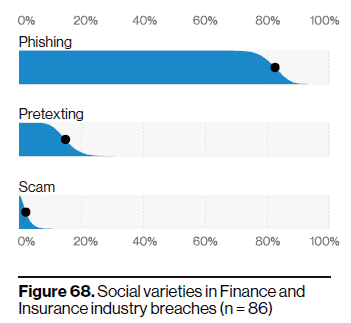
The Social varieties in Finance and Insurance industry breaches are quite high (> 80%) and the DBIR claims that this is due to the increasingly common business email compromise in its various forms. “Among its many incarnations is the
phishing email,” says the team, “Masquerading as coming from someone in the executive level of the company asking for something of monetary value.”
The Social varieties in Mining, Quarrying, and Oil and Gas Extraction (NAICS 21) with the Utilities (NAICS 22) industries shows that Social attacks such as Phishing and Pretexting dominate incident data.
It’s clear that Phishing is not going away and this blog post just scratches the surface of that attack vector. The 2020 DBIR goes into great detail on the other industries, geographies, and attacks but we wanted to leave you with some summary statistics from the report.
- 22% of breaches included Social attacks
- 70% of breaches were perpetrated by External actors
- 86% of breaches were financially motivated
We encourage you to download the full 2020 Verizon Data Breach Investigations Report (DBIR) and investigate the data yourself. As always, should you ever have any questions about phishing and/or testing your organization’s capabilities to recognize or defend against such attacks, please reach out to us.

Andrew Hay is the COO at Lares and is a veteran cybersecurity executive, strategist, industry analyst, data scientist, threat and vulnerability researcher, and international public speaker with close to 25 years of cybersecurity experience across multiple domains. He prides himself on his ability to execute the security strategy of the company with which he works without neglecting business objectives and the needs of its customers. Andrew is the author of multiple books on advanced security topics and is frequently approached to provide expert commentary on industry developments. He has been featured in publications such as Forbes, Bloomberg, Wired, USA Today, and CSO Magazine.